Cisco tablet hacking
Recently I got two units of Cisco Telepresence Touch 10 tablet, that I wanted to repurpose.


HW seems to be relatively capable with specs:
- CPU OMAP4460 @ 1.2GHz
- RAM 1GB DDR2
- eMMC 4GB
- Display 1280 x 800 (Innolux HD101IA-01U)
- Touchscreen ctrl CY8CTMA884LTI-13T
- PN544 NFC
- CC256x BLE
This device was manufactured from 2013 to ?? . There are 2 HW versions, this being the older one, which can be identified by onboard micro USB connector.
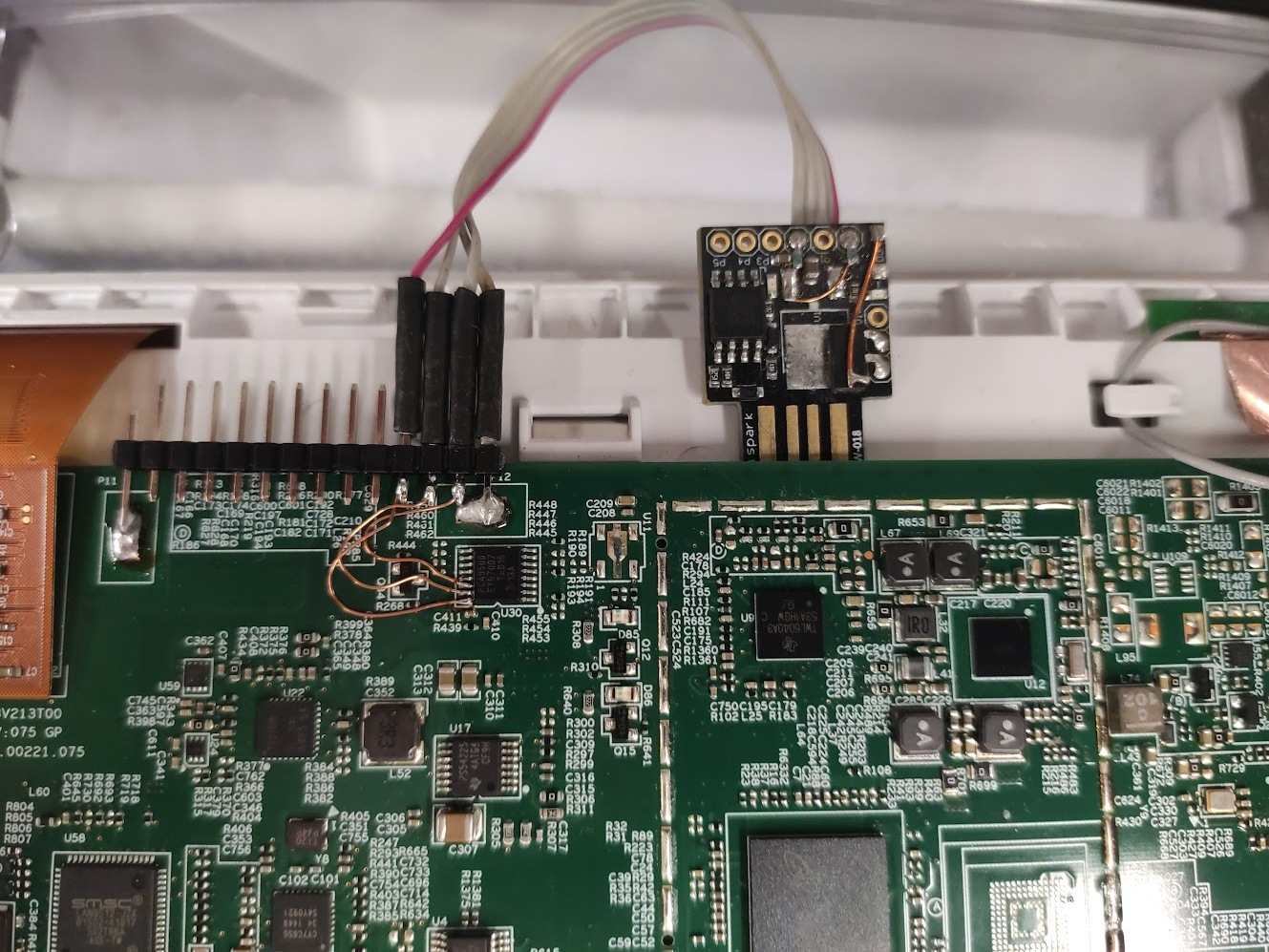
On board there is micro USB connector that goes to onboard FT230 USB to UART convereter. The same UART lines are accessible on the board via another connector. This is for UART TTY shell.
Only working login is "support" with blank pwd, but it's supportsh shell is highly limited in available commands, and none of them is capable of modifying anything.
Same goes for u-boot in which the CLI is disabled. I tried to avoid loading kernel by shorting out the eMMC data lines after the u-boot was loaded, hoping this will lead to failure and CLI spawn, but when the u-boot is unable to verify the kernel it restart the board.
After this I continued and removed the eMMC IC so I could dump it and analyze it. I used my KEIB boards with Pine64 USB eMMC adapter.
The dump can be downloaded here.
eMMC partition scheme:
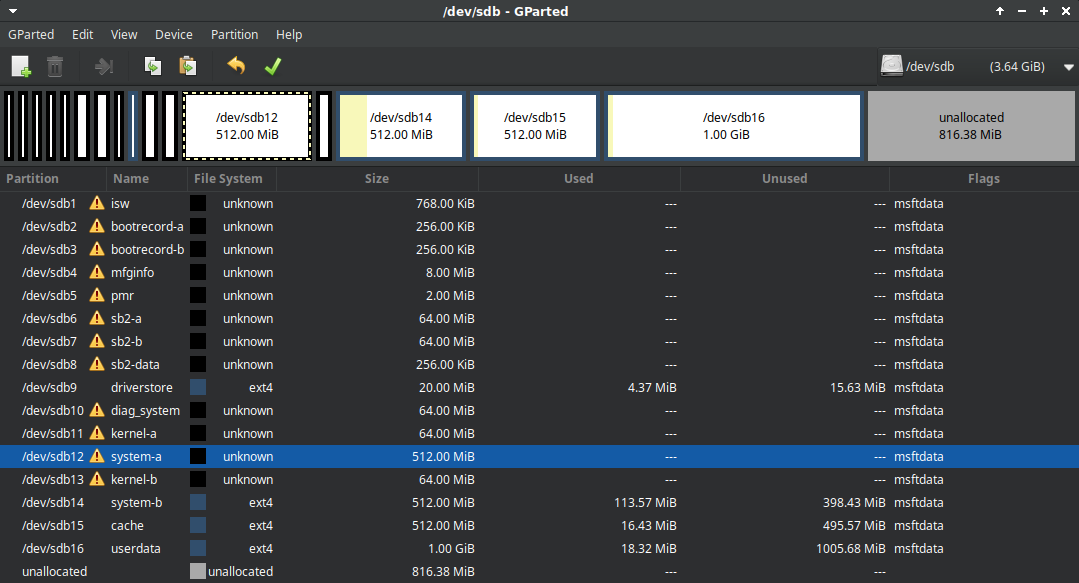
On the partition 14 there are things as rootfs image, and images for config, user data and more.
Unfortunately those are encrypted and the key is nowhere in sight.
By examining the partition content, we can find scripts and config files that are used to upgrade the data on the device and for that they need to be decrypted.
rwfsfunctions script (stripped):
if findkey "$key" | \
mount -p0 -o loop,encryption=aes $fs $tmpdir 2>/dev/null; then
# All is well
umount $tmpdir
echo "Skipping usable file system"
return 0
fi
Here the findkey function is missing, but after using binwalk to extract rootfs which is unencrypted we can find findkey in rootfs bin folder.
findkey:
#!/bin/sh
# Argument is on format
# filename@offset:size
key="$1"
[ -z "$key" ] && exit 0
keyfn=`echo $key | cut -f1 -d@`
keyoffset=`echo $key | cut -f2 -d@ | cut -f1 -d:`
keysize=`echo $key | cut -f2 -d@ | cut -f2 -d:`
dd if=$keyfn skip=$keyoffset bs=1 count=$keysize 2>/dev/null
rwfs.conf:
RWFS_KEY=/sys/class/i2c-adapter/i2c-4/4-0054/eeprom@101:16
RWFS_KEYMAGIC=/sys/class/i2c-adapter/i2c-4/4-0054/eeprom@96:5
RWFS_KEYWP=/sys/class/gpio/gpio137/value
RWFS_ENABLE_WP=0
RWFS_DISABLE_WP=1
RWFS_FS="config,4 user,4"
partitions.conf.d/rwfs:
config.img /config rw,key=/sys/class/i2c-adapter/i2c-4/4-0054/eeprom@101:16,save
user.img /user rw,key=/sys/class/i2c-adapter/i2c-4/4-0054/eeprom@101:16,save
So to summarize, now we know that the images are encrypted with AES and the key is stored on the I2C EEPROM with address 0x54 and its 16 bytes starting from offset 0x65. Yaay.
Next we need to extract the key from onboard EEPROM.
There is no dedicated EEPROM in common package as SO-8, but there is PCA9500 I2C IO expander with integrated 2-Kbit EEPROM.
On the board I soldered pinheader and used insulated wire to connect Vcc, SDA, SCL and GND on it. I used I2C-Tiny-USB to probe and then read the memory content.
Expander+EEPROM with soldered wires and the adapter:
i2cdetect:
:~$ i2cdetect -y -a 17
0 1 2 3 4 5 6 7 8 9 a b c d e f
00: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
10: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
20: -- -- -- -- 24 -- -- -- -- -- -- -- -- -- -- --
30: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
40: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
50: -- -- -- -- 54 -- -- -- -- -- -- -- -- -- -- --
60: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
70: -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
i2cdump:
:~$ i2cdump -y 17 0x54
No size specified (using byte-data access)
0 1 2 3 4 5 6 7 8 9 a b c d e f 0123456789abcdef
00: 04 ff cb 92 43 54 53 2d 43 54 52 4c 2d 44 56 31 ?.??CTS-CTRL-DV1
10: 30 20 20 20 20 20 89 56 30 31 20 c1 8b 46 4f 43 0 ?V01 ??FOC
20: 31 39 32 36 4e 30 59 55 cf 06 88 43 e1 c6 c2 df 1926N0YU???C????
30: 43 00 01 49 00 00 c0 46 00 4a 01 88 3b 02 8d 43 C.?I..?F.J??;??C
40: 30 20 20 ff ff ff ff ff ff ff ff ff ff ff ff ff 0 .............
50: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
60: 31 36 4b 45 59 b3 e1 00 6a 08 5b 9f ae da d3 3c 16KEY??.j?[????<
70: de 26 67 f4 6e ff ff ff ff ff ff ff ff ff ff ff ?&g?n...........
80: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
90: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
a0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
b0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
c0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
d0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
e0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
f0: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff 5b ...............[
Therefore our key should be:
0xb3 0xe1 0x00 0x6a 0x08 0x5b 0x9f 0xae 0xda 0xd3 0x3c 0xde 0x26 0x67 0xf4 0x6e